So, let’s see if I understand, the device only destroys the data after it’s connected to a computer.
So an adversary can just not connect it to a computer and extract the data through alternative means (like unsoldering the chip and reading it directly.
The device should be able to destroy itself either from an internal battery or some physical or chemical mechanism.
My assumption is that it probably uses the same mechanism that most other SSDs already have where it always saves the data with internal encryption and simply overwrites the encryption key when a wipe is requested.
This same mechanism already allows SSDs to be formatted quickly while still being secure without having to zero out everything, which would cause a lot of additional wear.
The additional complete wiping would just be the cherry on top.
deleted by creator
if you’re using proper encryption it’s going to be difficult or impossible to decrypt the files on the drive, so the data should be secure even if the drive is stolen, copied, etc.
Encryption should always be the last line of defence, encryption that is unbreakable today may be trivially broken tomorrow. Which is why I also I still prefer to overwrite drives with random data instead of just trusting the sanitise command (Even though I know that a big chunk of the data stays unoverwritten as part of the drive’s “provisional area”.
(Which raises another issue that “deleting” a luks keyslot or the whole header doesn’t actually warranty it’s deleted, may have just be moved to the provisional area. So if a key somehow is compromised it becomes nessesary to physically destroy the drive.)
However, when you’re actively using the drive and have files decrypted, and then you lose physical access to your devices, you have a problem. IIRC that’s how they got Ross Ulbricht’s files - monitored him until he unlocked his laptop in a cafe and then grabbed it (and him). If you’re worried about that specific threat profile it makes a little more sense to have an easily accessible physical DELETE EVERYTHING NOW button that only operates when the drive is running.
In that case I rather use something that will reboot the computer and shred the ram as it would serve the same purpose with the bonus that contents can’t also be recovered from ram. Something like an usb drive with a string wrapped around the wrist.
Now, in the situation that the keys have leaked somehow, (like recording the keyboard from afar while the user types the passphrase) then the self-erasing hard drive makes a lot more sense, assuming the user has time to trigger the mechanism.
Now the issue is, that overwriting even a fast ssd takes time, so I’m assuming the device works by destroying or erasing a security chip that holds the keys for the main storage, however the data is still there if the adversary cuts the power before overwriting the whole drive. Ofc encrypted, but like I said before, encryption may be broken tomorrow. A physical or chemical solution that grinds or dissolves the chip somehow seems to me a better option, with the bonus that it can be made to work without electricity.
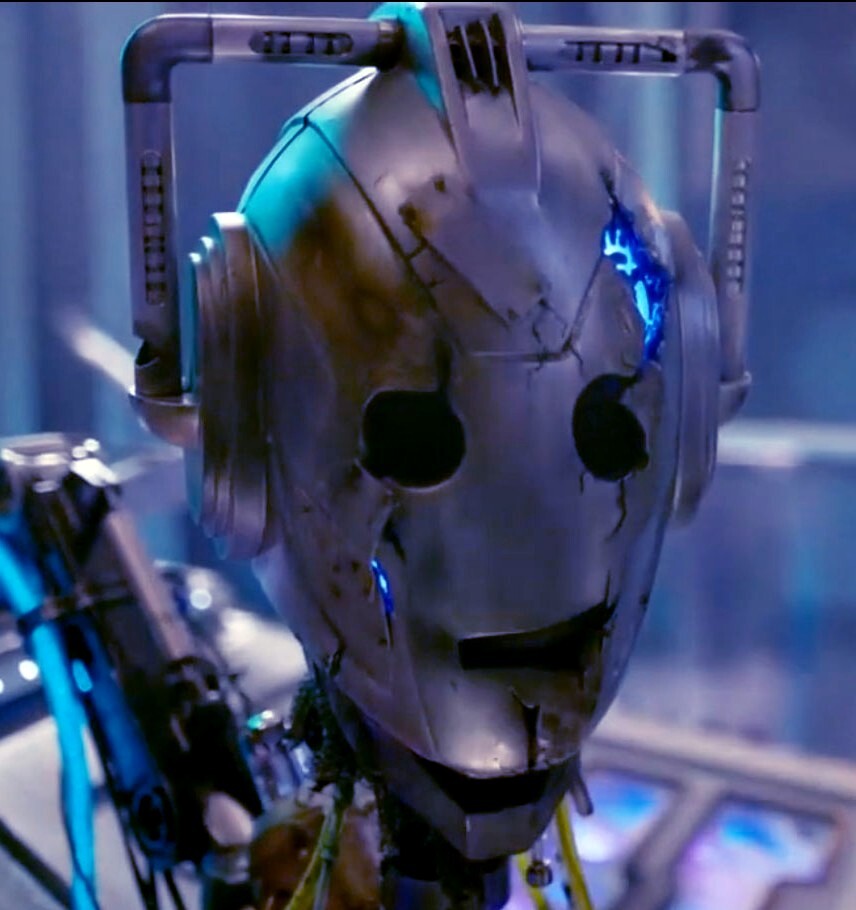
The image you posted seems to disagree with you. There is some sort of “Physical Data Destruction” in phase 2. The article says the switch breaks some chips, but I didn’t get much beyond that. In any case, lets hope the delete-when-plugged-in thing is redundant.
So it’s a fidget with a slider AND a button?
Two stage slider
Or you could just use an encrypted file system…
If they are willing to torture you for the decryption key, then they are also willing to kill you if you destroy the drive.
Def not true about the justice system, killing you does not do them any good, they just want good prosecution statistics
What we really need is encryption with a duress password that just shows some harmless files. Maybe have it overwrite the sensitive data if they want to verify size of the drive. Does something like that already exist? I know standard duress password does, but that could go down as destruction of evidence.
TrueCrypt had/has that feature for full-drive encryption. But I don’t think anyone serious uses them anymore due to the current code maintainers having some questionable allegiances.
Truecrypt is followed by VeraCrypt which is now the standard. Don’t use TrueCrypt
You can embed encrypted data inside media files like video, image and audio files. Thats your best bet i think. You cant really hide an entire filesystem afaik unless you build a custom storage device with a controller that only physically connects certain sections under specific conditions.
Help, my cat stepped on the button, how do I recover my data?
To prevent accidental and catastrophic presses, the drive’s self-destruct button is designed with a two-stage sliding switch.
Looks like they prevent that.
CATastropic preesses are prevented? Sounds PURRfect.
I’m not sure I trust myself with that functionality.
Fatal flaw is it has to be connected to a computer to start the process. If someone truly wants the data they could just disassemble the device before it gets connected if the button has been pressed. They should have found a way to do it with a small onboard battery reserved only for that purpose.
I mean, it could just be a capacitor. It’s easier to fry something than make it delete itself
Capacitor wouldn’t allow long enough to wipe the data first. It’s a two pass system. Wipe data then destroy. Also capacitors lose charge over time much, much more quickly than a battery. You still would need to have plugged it in very recently. And yes to build enough voltage to destroy electronics physically and quickly with a battery, it would actually probably need both battery and capacitors anyway which would also increase size. I’m guessing it was a tradeoff of size vs functionality, but having it not work until it’s plugged in after pressing the button which is bright red when pressed, seems like a very simple way to bypass the destruction by simply disassembling it before plugging it in. Only good if the thief/agent doesn’t know why there’s a big red spot on it before plugging it in, which is a bad assumption for security especially if you deploy these widely so everyone knows what they are.
Why are you wiping the data? Why not just slag the whole chip… Hard to read an SSD in liquid form
What if the destruction fails, or isn’t thorough. Much harder to retrieve information from a partial block of memory if it has also been overwritten with garbage to erase it. Redundancy is essential to security.
A device like that isn’t putting enough voltage into it to “melt” it. It you want it that well destroyed you’re going to need a high temperature incinerator with a good filter since it’s not safe to breath the smoke it will create. Or at the very least a heating element inside it, but then you need layers of heat protection so it doesn’t catch everything around it on fire or burn the person pushing the button.
This isn’t that. This is meant to destroy the data at a moment’s notice with the push of a button. Problem is that it has to be plugged in to do it, which in my mind is defeating the purpose.
I mean, you could probably pick two strategic pins and fry the wells… You might have to do a few of them to make sure that your hit every bank. If you blow through the insulation between them, I can’t imagine any method could recover the data. And it shouldn’t take much current
The liquid thing was just because… You know, solid state drive
Yeah, but again, that requires precise destruction in a cheap chip while making sure both not to do it accidentally and making sure it’s successful afterwards. With redundancy, if one thing fails, there’s something else to do the job. Most corporations have abandoned this idea in exchange for short term profit and planned obsolescence. But it’s actually super important in real security.
But like… You could just make it physical. Put a couple extra leads on the PCB, charge the capacitor, and let the button close the circuit mechanically. You might have to do a couple tests, but that’s better than having storage with a delete button on it
What does a delete button add? It’ll take minutes. Might as well put an e-stop button on your desk that connects to your computer by USB
It’s basically security theatre
Oops.
My friends kid loves to press the power button on her computer. This looks too tempting. haha
kinda like the recompute base encryption hash button in sales guy vs web dude